Preview of the Policy Management UX
Azure Resource Manager policies provide the ability to manage risks within a Azure environment. To implement this so called policies can be created to enforce specific circumstances.
One of my previous post: “Define Azure Resource Manager Policies” describe what policies are. Some key features are:
- Polices are a settings that are default set to allow.
- Policies are described by policy definitions in a policy definition language (if-then conditions).
- Polices are defined with JSON formatted files.
Policy Management UX
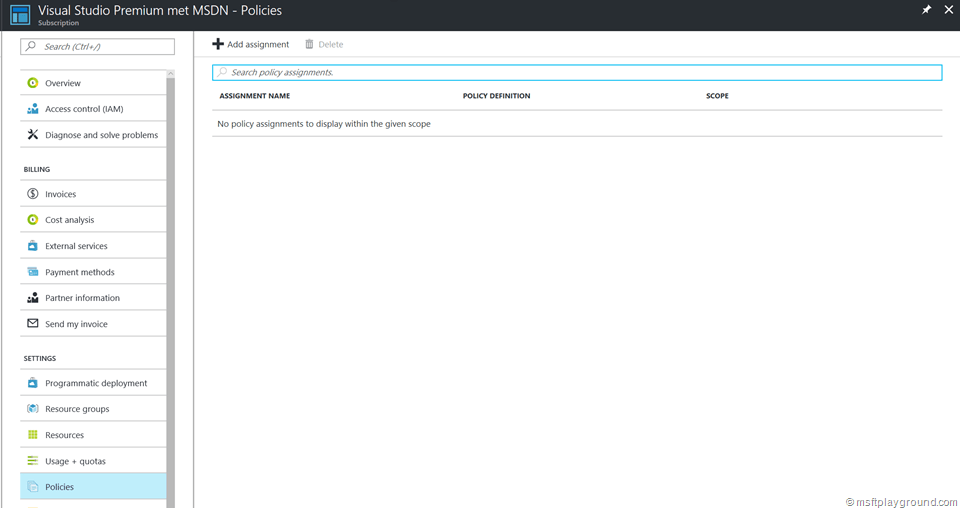
As of today policies can be managed within the Preview Azure Portal. Before this you needed to use PowerShell (If you prefer PowerShell you can read my previous post: “Define Azure Resource Manager Policies”). For a couple situations you still need to use PowerShell because certain functions are not yet available within Azure.
With the Policies UX you can view the policy assignments on two levels:
- Subscription
- Resource Group
A option "Policies" is added to the settings blade of the specified levels. Clicking on the setting will show the assigned policies.
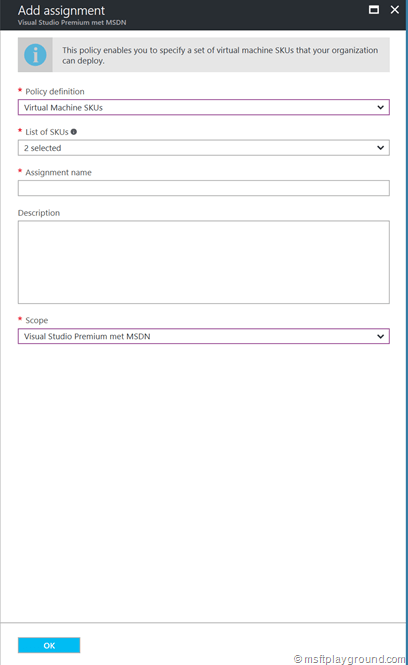
By clicking “Add assignment” you can add policy assignments. The policy UX offers a couple of build-in options:
- SQL Server version 12.0 required.
- Allowed resource types.
- Not allowed resource types.
- Storage account SKU’s.
- Storage account encryption required.
- Virtual Machines SKU’s.
- Allowed locations.
The build-in options provide you with the ability to add the specific allowed items directly from the interface for example the SKUs of Virtual Machines.
Besides the build-in policies the drop down also shows custom policies that are uploaded via PowerShell.
Conclusion
The policy management UX is a great starting point for doing more with policies. Policies are not used that often and this UX will help to get started. In the near future the UX should be extended because it is lacing some commonly used functionalities. Besides the UX I hope that they enhance the policy definitions. In my opinion some enhancements should be:
- Better error messages within the portal, that reference the policies.
- A way to edit the policies within the portal.
- Management across subscriptions.
- Tagging with policy definitions.
- Uploading custom policies.
- Regular expression possibility within policies. This can come in use for naming conventions.