Define Azure Resource Manager Policies
Azure Resource Manager policies provide you with the ability to manage risk within you Azure environment. You can write policies to enforce certain situations.
- A policy setting is default set to allow.
- Policies are described by policy definitions in a policy definition language (if-then conditions).
- You create polices with JSON formatted files.
Policies that you have defined can be assigned to certain scopes:
- Subscription
- Resource Group
- Resource type
Within the definition of the policies you can define the below actions:
- Deny: Blocks the resource request
- Audit: Allows the request but adds a line to the activity log. These can be used to start action within Azure Automation.
- Append: Adds specified information to the resource. For example tagging the resource with useful information.
I started to create Azure Resource Manager Policies and created a GitHub repository to save them and share them.
Within this repository you have the option to add policies and work together on them to get a default set of policies.
The repository also contains a script files to assign the policies to specific resources.
Implementation
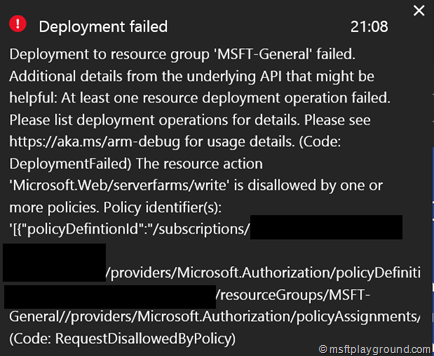
One of the policies within the repository is a policy to ensure that resources are created within the Europe regions.
The policy is described in if-then conditions, if the resource is not created in West-Europe (westeurope) or North-Europe (northeurope) the creation of the resource will be declined (deny).
{
"$schema": "http://schema.management.azure.com/schemas/2015-10-01-preview/policyDefinition.json",
"if": {
"not": {
"field": "location",
"in" : ["northeurope" , "westeurope"]
}
},
"then": {
"effect": "deny"
}
}
In the policy file the schema file specified to get type-ahead functionality within JSON editors.
This policy can be assigned to a resource with executing two PowerShell commands:
- New-AzureRmPolicyDefinition
- New-AzureRmPolicyAssignment
With the first command the definition is created, and saved to a PowerShell object.
$policy = New-AzureRmPolicyDefinition -Name [Policy Name] -Description [Policy Description] -Policy [Path to Policy JSON File]
The second command is then used to assign the policy to a certain scope.
New-AzureRmPolicyAssignment -Name [Policy Name] -PolicyDefinition $policy -Scope [Scope]
Putting everything together and making the script as generic as possible you have the following script to assign a policy to a resource group.
$policyName = Read-Host "Specify the name of the policy"; $policyDescription = Read-Host "Specify the description of the policy" $policyFile = Read-Host "Path to json policy file"; $resourceGroup = Read-Host "Specify the resource group"; #Login to the Azure Resource Management Account Login-AzureRmAccount #Let the user choose the right subscrition Write-Host "---------------------------------------------------------------------" Write-Host "Your current subscriptions: " -ForegroundColor Yellow Get-AzureRMSubscription Write-Host "Enter the Subscription ID to deploy to: " -ForegroundColor Green $sub = Read-Host Set-AzureRmContext -SubscriptionId $sub clear $subId = (Get-AzureRmContext).Subscription.SubscriptionId $subName = (Get-AzureRmContext).Subscription.SubscriptionName Write-Host "Policy is applied to the resource group: $resourceGroup in subscription: $subName" $policy = New-AzureRmPolicyDefinition -Name $policyName -Description $policyDescription -Policy $policyFile; #Assign the Azure Policy New-AzureRmPolicyAssignment -Name $policyName -PolicyDefinition $policy -Scope "/subscriptions/$sub/resourceGroups/$resourcegroup"
After assigning the policy and trying to create a resource in another region will result in a error message. Sometimes this can still be a really descriptive message as shown in the image below.