Creating a Logic App API Connection that uses the Managed Identity using Bicep
Logic Apps in Azure provides a platform for building workflows that integrate with various services and APIs. When creating Logic Apps, you must often connect securely to other services like the Azure Service Bus and Azure Storage Accounts. Managed Identity is a recommended way to accomplish this.
Creating these API Connections with Infrastructure as Code isn't documented well and is challenging to figure out. It took me some time, but I figured it out by looking at the API requests that the portal does.
Figuring it out
The steps I have taken to figure it out can be applied in different scenarios for Logic Apps but, for example, also on other parts of the portal.
- Create a new Logic App in the Azure portal.
- Add an Identity to the Logic App and give that identity access to the Azure Service you want to use. In this example, we will be using an Azure Service Bus.
- Add a Service Bus trigger to the Logic App and fill in the information below.
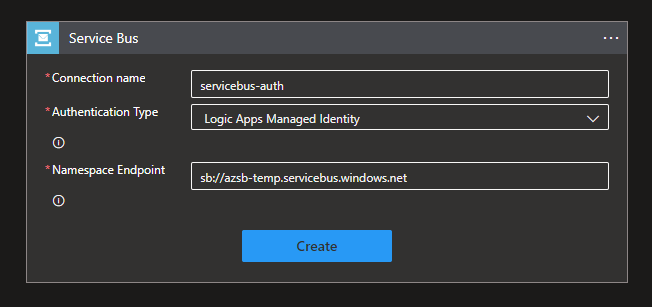
- Before you click 'create,' open de Edge DevTools (F12) and open de network tab
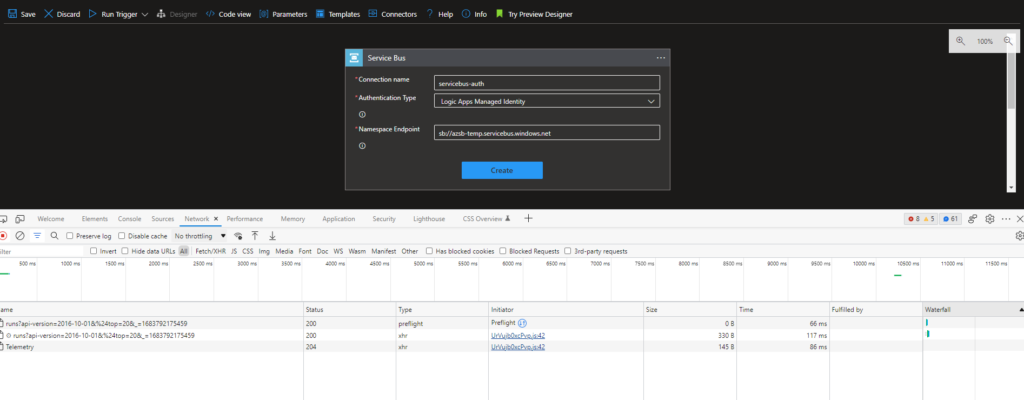
- Clear the network items list and click 'Create.'
- When the trigger is refreshed, stop the network trace and search for an item that puts information into Azure. When using the Service Bus, the item will look like below.

- On the right side of the network trace, click on the Payload tab to find the information sent to the Azure Resource Manager. This contains the information that needs to be used in Bicep.
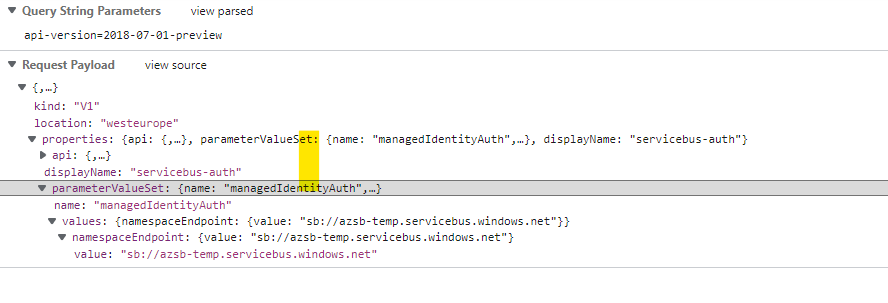
{
"id": "/subscriptions/f124b668-7e3d-4b53-ba80-09c364def1f3/providers/Microsoft.Web/locations/westeurope/managedApis/servicebus",
"parameterValueSet": {
"name": "managedIdentityAuth",
"values": {
"namespaceEndpoint": {
"value": "sb://azsb-temp.servicebus.windows.net"
}
}
},
"displayName": "servicebus-auth",
"kind": "V1",
"location": "westeurope"
}
The outcome in Bicep
With the findings, the specific Bicep code can be written. Below are three different API connections that use Managed Identities for the connection.
Azure Storage Account API Connection with Managed Identity
resource storageaccountApiConnectionAuth 'Microsoft.Web/connections@2016-06-01'= {
name: 'azuretables-auth'
location: location
properties: {
api: {
id: 'subscriptions/${subscription().subscriptionId}/providers/Microsoft.Web/locations/${location}/managedApis/azuretables'
}
parameterValueSet: {
name: 'managedIdentityAuth'
values: {}
}
displayName: 'azuretables-auth'
}
}
Azure Service Bus API Connection with Managed Identity
resource azla_apiconnection_servicebus_auth 'Microsoft.Web/connections@2016-06-01' = {
name: 'servicebus-auth'
location: location
properties: {
displayName: 'servicebus-auth'
api: {
id: subscriptionResourceId('Microsoft.Web/locations/managedApis', location, 'servicebus')
}
parameterValueSet: {
name: 'managedIdentityAuth'
values: {
namespaceEndpoint: {
value: 'sb://${serviceBus}.servicebus.windows.net/'
}
}
}
}
}
I hope that this helps you in creating epic Bicep files. If you are looking for more information, be sure to look at the following:
