Securing applications with the Azure Key Vault and Azure DevOps
When developing applications for Azure security it always one of the items you need to cross of your list. Many security requirements can be solved by embedding the Azure Key Vault within your application. The Azure Key Vault can help you solve the following problems:
- Secrets Management
- Key Management
- Certificate Management
- Store secrets backed by Hardware Security Modules
If you centralize the secrets in a Key Vault it allows you to control the distribution of those secrets and also manage who is allowed to get, list (many more actions) these secrets. In the most perfect situation a team member of the DevOps team does not even know those secrets. He only deploys the Azure resources via an Azure Pipeline and the rest is managed by another team. The only thing that needs access to the Key Vault in this situation is the application used by the Azure Service Connection.
To make the actions against the Azure Key Vault more easy I developed a extension called "Azure Key Vault actions" with this extension added to your build or release pipeline these actions can be performed:
- Get Azure Key Vault secret value
- Add / Update Azure Key Vault secret
- Remove Azure Key Vault secret
- Add access policy
- Remove access policy
- Import Azure Key Vault certificate
- Get Azure Key Vault certificate Url
This extension solves a problem for maintaining and deploying large environments with Azure DevOps. For example an environment that you are deploying uses Azure App Services with a managed identity. This Identity may need automatic access to the Key Vault to retrieve secrets.
In Azure DevOps there is a default integration with the Azure Key Vault. I found that this integration does not offer all the actions that you may want to carry out.
Getting started
To get started with the extension follow the below steps.
- Go to the Azure DevOps market place: https://marketplace.visualstudio.com/azuredevops
- Search for the extension: “Azure Key Vault actions” or use this direct link: https://marketplace.visualstudio.com/items?itemName=maikvandergaag.maikvandergaag-azurekeyvault
- Click on the “Get It Free” button and follow the installation instructions for the extension.
Azure Key Vault actions task
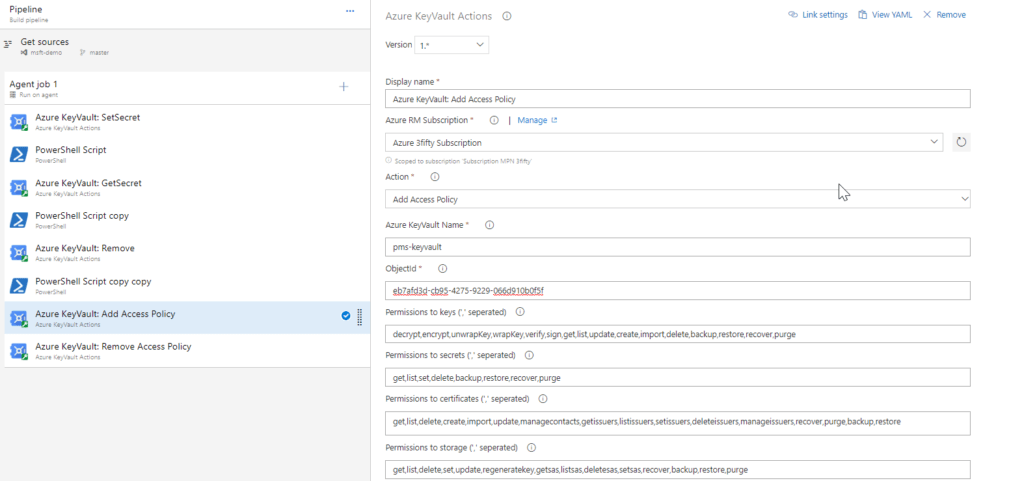
With the task installed it can be added to a Build or Release pipeline. Depending on the actions you choose you need to fill in the following properties:
- Azure RM Subscription: The subscription / service connection to connect to.
- Action: The specific action to perform on the specified Key Vault.
- Key Vault name: The name of the key vault.
- Secret name: The name for the secret.
- Secret: The secret value, for this value you should use a secured variable within Azure DevOps Pipelines.
- Certificate name: Name of the certificate to retrieve or import.
- Certificate file: The certificate file to import.
- Certificate password: The password of the certificate.
- ObjectId: The objectId of the object in Azure Active Directory to give access to or remove from the access policies.
- Permissions to keys: Permissions to the keys separated by ','
- Permissions to secrets: Permissions to the secrets separated by ','
- Permissions to certificates: Permissions to the certificates separated by ','
- Permissions to storage: Permissions to the storage separated by ','
- Variable name: The name of the variable to save the results to.
- Overwrite: Overwrite the secret or certificate if it already present is in the Key Vault.
The task needs a Azure RM Subscription endpoint. The endpoint uses a Azure Active Directory application in the background. When using the task make sure this application has the appropriate role assignments on the Azure Key Vault (role assignment: owner).
Support
I maintain the extension in my free time and the sources of the extension can be found GitHub. If you encounter any issues or would like to see different features, please let me know by adding an issue to GitHub repository.
Extensions
Besides this extension I created several others. More information about these extension can be found here: