The securitydata Azure resource group
Most of the times companies have rules in place for managing their Azure environment. The main rules that should be in place are “Azure Policies” and naming conventions. Naming convention should be used to easily identify Azure resources and making consistency within the Azure Portal. These naming convention could then also be written up into policies to make sure everyone is being compliant.
To get started with the naming conventions you can take a look at the following article of Microsoft:
Resource Group naming convention
Most of the time (depending on the subscription setup) I use the following naming convention for the resource groups:
<environment>-rg-<shortname>
With this naming convention I can easily identify the resource group and also know for which environment it is. In a project we used the Azure Security Advisor and saw a resource group named “securitydata” appearing with a storage account in it. To comply with the rules we deleted the resource group and saw it appearing a few hours later.
Removing the securitydata resource group
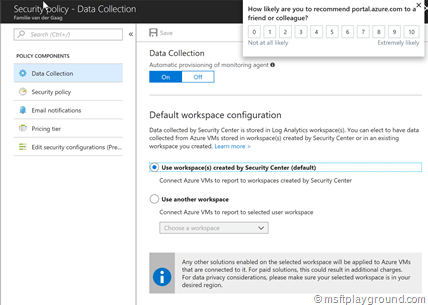
Because the group kept appearing we looked into another option. The security advisor uses the storage account for saving data it found during the data collection. If you look at the data collection blade of the security advisor you see that there are two options:
- Use workspaces created by Security Center (default).
- Use another workspace
The first option makes use of the storage account and the second one is bound to a “OMS” workspace. We already had a OMS workspace within our subscription so we bound the data collection to that workspace. If you do not have a OMS workspace you can easily created (it is also a free service depending on the abilities you use).
To get everything in place follow the below steps:
- Create a Log Analytics service (OMS) if you don’t have one. Make sure that you apply the naming convention rule
 .
. - Navigate to the Security Advisor.
- Within the Security Advisor blade click on “Security Policy”.
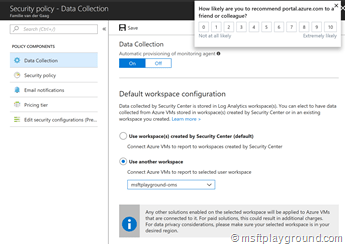
- Click on the subscription for which you want to collect data.
- On the data collection blade, bind the security advisor data collection to your OMS workspace.
- Save the changes
- In the “Pricing tier” blade check if the correct tier is selected.
- When done delete the “securitydata” resource group.

![clip_image001[14] clip_image001[14]](/assets/archive/2018/04/clip_image00114_thumb.png)