Managing access control for Logic Apps
In some situations access to the workflows needs to be controlled. This has to be done in some way to make sure only specific people can trigger or see the content of it. These situations are mostly applied to Logic Apps that can be triggered via a external endpoint.
One of the most known options is the Integration Service
Environment which also gives the option of connecting your Logic App to your
private virtual network., but this post will not go into any details about this
but will focus on the true PAAS options. If you want to know more about integration
service environment read this post:
Access Control Control Configuration
Within the "Workflow Settings" the access control for a Logic App can be managed. Via this configuration you have three options of providing access to the workflow.
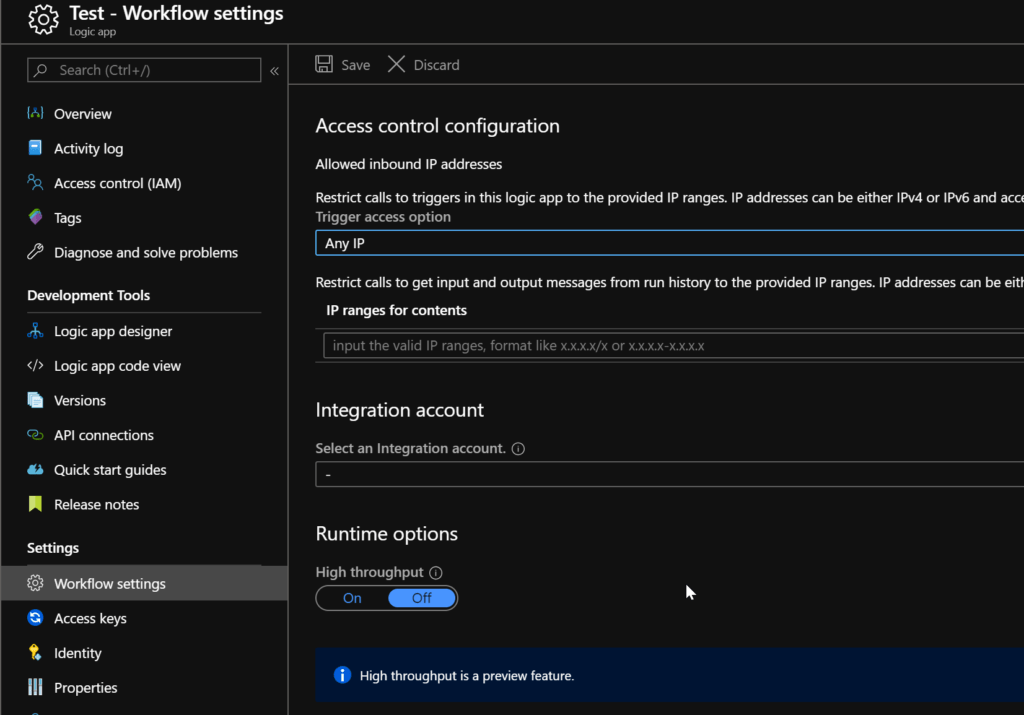
Any IP
By default "Any IP" is selected for a Logic App . As you might think this option allows traffic from any location.
ARM
This option does not require any specific configuration within a ARM template of a Logic App.
IP Ranges
The second option within the access control configuration is “Specific IP ranges”. This option will allow access and content restriction to the specified IP ranges.
ARM
Allowing access to specific IP ranges can be done for triggers, actions and content. Content will be mentioned in the last paragraph.
"resources": [
{
"name": "[parameters('LogicAppName')]",
"type": "Microsoft.Logic/workflows",
"location": "[parameters('location')]",
"tags": {},
"apiVersion": "2016-06-01",
"properties": {
"definition": {},
"parameters": {},
"accessControl": {
"triggers": {
"allowedCallerIpAddresses": [
{
"addressRange": "10.0.0.0/24"
}
]
},
"actions": {
"allowedCallerIpAddresses": [
{
"addressRange": "10.0.0.0/24"
}
]
}
}
}
}
]
Only other Logic Apps
Another option within Logic Apps is “Only other Logic Apps”. This option restricts trigger access to only other workflows within Azure. This scenario is mainly used when you are creating Logic Apps and have specific actions that are handled by a separate workflow.
ARM
Restricting a Logic App trigger to only other Logic Apps is done by not specifying any IP ranges within the ARM configuration.
"resources": [
{
"name": "[parameters('LogicAppName')]",
"type": "Microsoft.Logic/workflows",
"location": "[parameters('location')]",
"tags": {},
"apiVersion": "2016-06-01",
"properties": {
"definition": {},
"parameters": {},
"accessControl": {
"triggers": {
"allowedCallerIpAddresses": []
},
"actions": {
"allowedCallerIpAddresses": []
},
"contents": {
"allowedCallerIpAddresses": []
}
}
}
}
]
IP ranges for contents
Within Access control configuration there is also an option restrict access and calls to get the input and output messages from run history to a specific range of IP addresses. This will disallow access to IPs that are not allowed to see the content within the run history which is a interesting option for Logic Apps with specific data.
ARM
Setting content restriction can also be done via ARM by specifying the the "contents" object within the access control of the resource template.
"resources": [
{
"name": "[parameters('LogicAppName')]",
"type": "Microsoft.Logic/workflows",
"location": "[parameters('location')]",
"tags": {},
"apiVersion": "2016-06-01",
"properties": {
"definition": {},
"parameters": {},
"accessControl": {
"triggers": {
"allowedCallerIpAddresses": [
{
"addressRange": "10.0.0.0/24"
}
]
},
"actions": {
"allowedCallerIpAddresses": [
{
"addressRange": "10.0.0.0/24"
}
]
},
"contents": {
"allowedCallerIpAddresses": [
{
"addressRange": "10.0.0.0/24"
}
]
}
}
}
}
]
