Restricting access to your Azure Web Application
As you may know almost everything that is deployed to Azure is publicly available. As with Azure SQL Database you do not have a firewall available for Azure Web Applications. That means other options need to be used to restrict access to Azure Web Application.
Restrict access by IP
A possible option is to restrict access to your application by IP addresses. The IP addresses can be added as a allowed IP address within the web.config of your application. All other IP addresses will get a 403 Forbidden response from Azure.
<system.webServer>
<security>
<ipSecurity allowUnlisted="false">
<clear />
<add ipAddress="99.99.99.99" allowed="true" />
</ipSecurity>
</security>
</system.webServer>
Restrict access for specific Users
Another option is to restrict access by enabling Authentication on the web application. This can be done for several Authentication Providers like: Azure Active Directory, Google, Facebook, Twitter and Microsoft. The below steps will help you with the configuration of Azure Active Directory as a authentication provider.
- In the Azure Portal navigate to the blade of the web application.
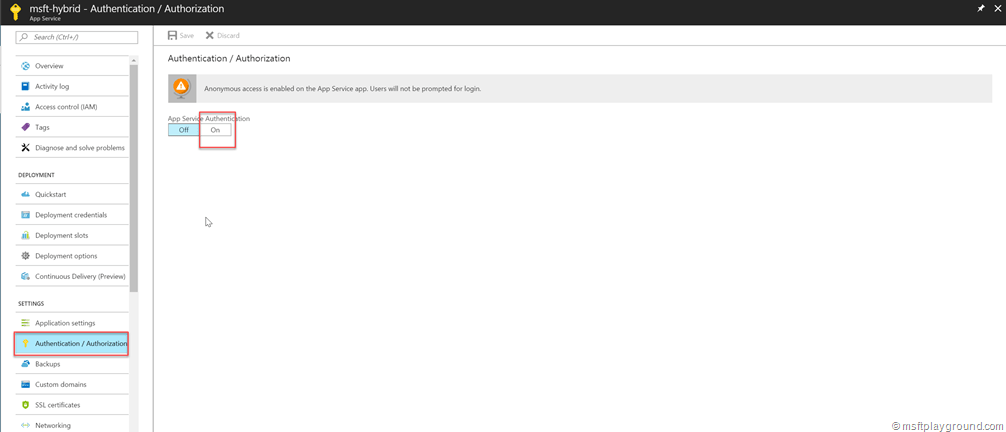
- Click on “Authentication/Authorization” and select “On”.
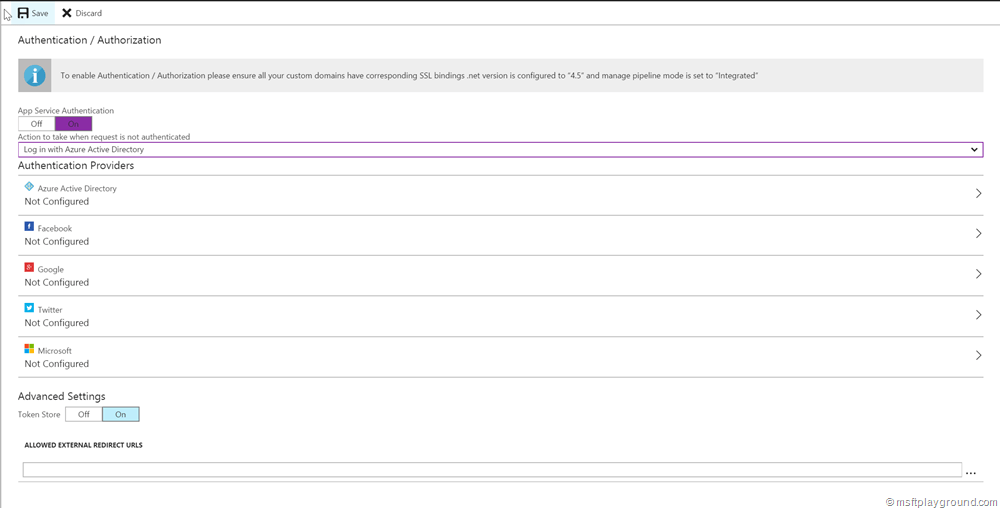
- Activating this option will give you several options for Authentication Providers. For know we will select Azure Active Directory.
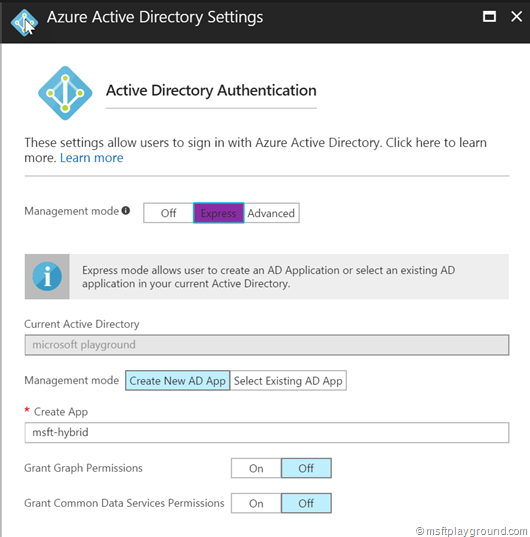
- Because there isn’t a pre-configured application select the “Express” option. This option will register the Enterprise application within Azure Active Directory for us, or let you select a existing.
- Clicking “Save” on this blade will register the application within Azure Active Directory. From there users can be granted access to the application.
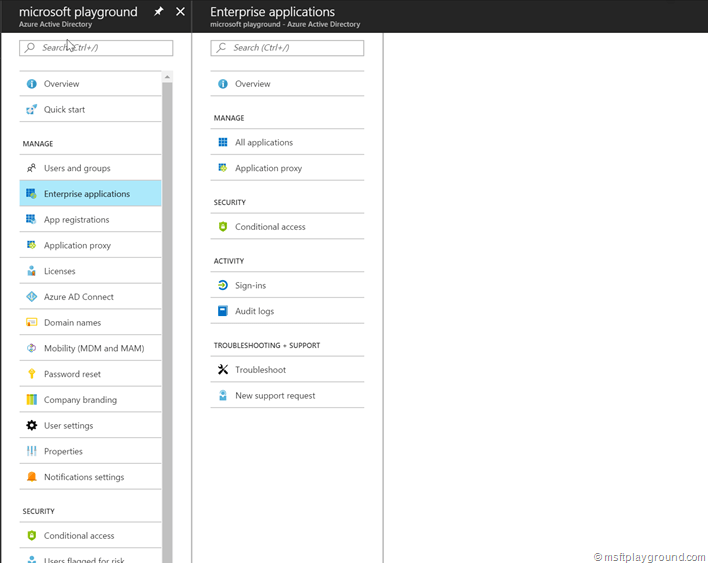
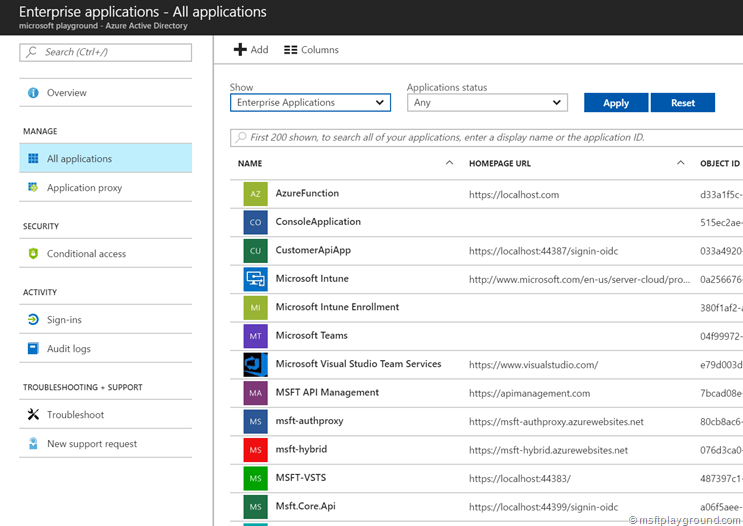
- To grant users access to the application open the Azure Active Directory blade within the Azure Portal and select Enterprise Applications.
- In the Enterprise Applications blade select “All Applications” to see a list of all applications that are registered within Azure Active Directory.
- From this list select the application. This will open the blade of the specific application.
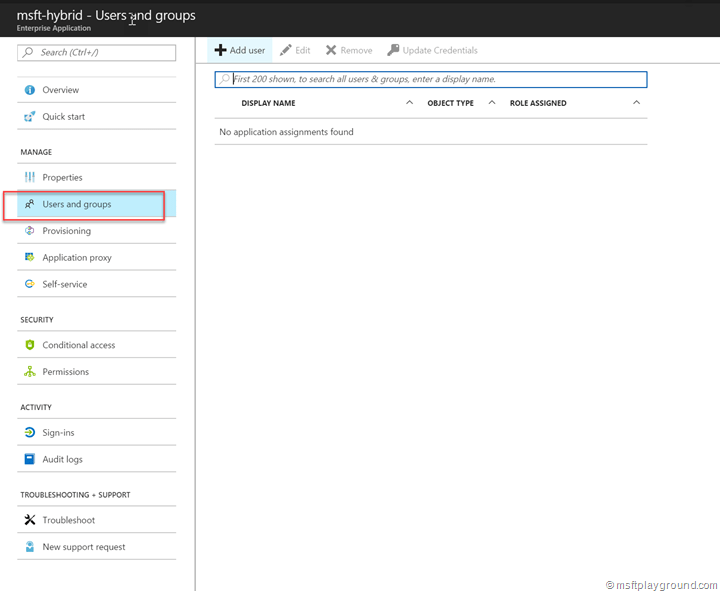
- In the blade select “Users and Groups”.
- In the “Users and Groups” blade all users are shown that are granted access to the application. From here you can a add users to give them access.
Restrict Crawling
When you are developing or testing a site that has anonymous content you probably want the content not to be crawled by spiders or bots because many traffic can come from bots and spiders. Stopping the crawling can be done by placing a file called “robots.txt” at the root of your web application with the following content.
#robots.txt User-agent: * Disallow: /