Securing an API app with an Application Identity–Part 1
Deploying an API within Azure is a very simple tasks. But how about security? The API itself is exposed to the outside world. When for example have a API app that is connected to on-premise systems with an Hybrid Connection the API will have to be secured in a certain way.
An option is to use Azure Active Directory. Within Azure Active Directory you can register an Application Identity for the API App. The connecting application will also have to be registered within Active Directory in order to connect to the API Application (This part will be discussed in part 2).
Part 1 will contain the setup of the API application in Part 2 the configuration and code changes for the client application will be discussed.
First off all the API app needs to be registered within Azure Active Directory. In order to manage Azure Active Directory the old Azure portal : https://manage.windowsazure.com needs to be used.
Azure Active Directory
Open up the Active Directory and click on the “Applications” tab.
In the bar at the bottom of the screen you can add a new application by selecting new. Selecting “New” will open a wizard for adding an application.
Select the option “Add an application my organization is developing”.
Enter the name of the application and since our application is an API app select “Web Application and/or Web API” and click next.
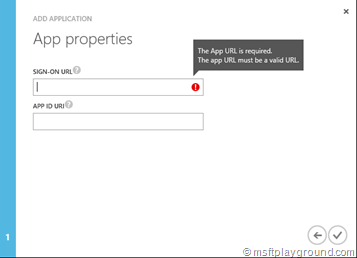
Fill-in a Sign-On URL if you do not have a specific sign-in URL fill in your default URL for example “https://example.com” (Note: The URL needs to be secured with SSL).
The APP ID URI is a URL specific for your tenant, this URL will need to contain the tenant name. It needs to be constructed in the following way: https://[tenant-name]/[app-name]
Save the options, the configuration screen of the application will be opened.
Code Changes
When the steps within Azure Active Directory are completed the API also needs some small code changes. To secure the application it self a couple of configuration need to be saved and we will save these in the web.config file.
<add key="auth:Tenant" value="[Tenant name, example.onmicrosoft.com]" /> <add key="auth:APPIDURI" value="[App ID URI of your API Application]" /> <add key="auth:TrustedCallerClientIds" value="[Trusted Callers ClientIds separated by ';']" />
- APPIDURI: APP ID URI of your application.
- Tenant:The name of the Azure AD tenant in which you registered the application ([tenant].onmicrosoft.com)
- TrustedCallerIds:The Client Id’s of the clients that are authorized to access the application separated by ‘;’.
In the “Startup” class register the Windows Azure Authentication mechanism.
public void ConfigureAuth(IAppBuilder app) {
app.UseWindowsAzureActiveDirectoryBearerAuthentication(
new WindowsAzureActiveDirectoryBearerAuthenticationOptions {
TokenValidationParameters = new System.IdentityModel.Tokens.TokenValidationParameters() {
ValidAudience = ConfigurationManager.AppSettings["auth:APPIDURI"]
},
Tenant = ConfigurationManager.AppSettings["auth:Tenant"]
});
}
Here you register your application and tenant for authentication. By these settings it will know on which tenant it is registered.
Next up it the API method itself. The methods within the API can be secured with a attribute called “Authorize”.
[Authorize]
public string Get(string id) {
if (string.IsNullOrEmpty(id))
throw new ArgumentNullException("id", "Argument 'id' cannot be 'null' or 'string.empty'");
//Get API
}
All of this together will make sure the application is secured. With a few additional steps you can also secure the application for specific caller applications. That is were the “TrustedCallersIds” configuration comes is.
From the ClaimsPrincipal of the caller application the client id can be retrieved. With the client id you check the values against the values saved within the web.config.
[Authorize]
public string Get(string id) {
Collection<string> trustedCallerClientId = AuthConfiguration.TrustedCallerClientIds;
string currentCallerClientId = ClaimsPrincipal.Current.FindFirst("appid").Value;
if (trustedCallerClientId.Contains(currentCallerClientId)) {
//Get API
}else{
throw new AuthenticationException("Client is not Authorized");
}
}
The “AuthConfiguration” class is a object that retrieves the Authentication settings from the web.config. The “TrustedClientIds” property retrieves the TrustedClientIds from the web.config.
public static Collection<string> TrustedCallerClientIds {
get {
List<string> retVal =new List<string>();
string ids = ConfigurationManager.AppSettings["auth:TrustedCallerClientIds"];
string[] itemIds = ids.Split(new string[]{";"}, StringSplitOptions.RemoveEmptyEntries);
retVal.AddRange(itemIds);
return retVal.ToCollection();
}
}

![image_thumb[20] image_thumb[20]](/assets/archive/2016/03/image_thumb20_thumb.png)
![image_thumb[28] image_thumb[28]](/assets/archive/2016/03/image_thumb28_thumb.png)